RSA 2005 Conference and Expo, San Francisco - Special Report
More than crypto systems and algorithms, the RSA conference and expo has become a premier showcase of the full spectrum of security products and concerns in this era of every more insecure computing.
This reflects growing in interest for security products at government and businesses everywhere. More attendees [about 13000] and more exhibitors were on-hand than ever before [over 275 companies and organizations before the conference started] for this 14th annual RSA conference.
And one trend more than any other may offer some respite from the growing tsunami of malware and identity theft: Trusted Computing.
The specifications developed over the last few years by the Trusted Computing Group [TCG] are now starting to implemented by major PC and software firms, most significantly motherboard crypto for PCs and notebooks from HP and IBM that identify users prior to bootup. Follow this link for the TGC presentations at RSA2005 [first 3 items]:
https://www.trustedcomputinggroup.org/downloads/tcg_presentations/
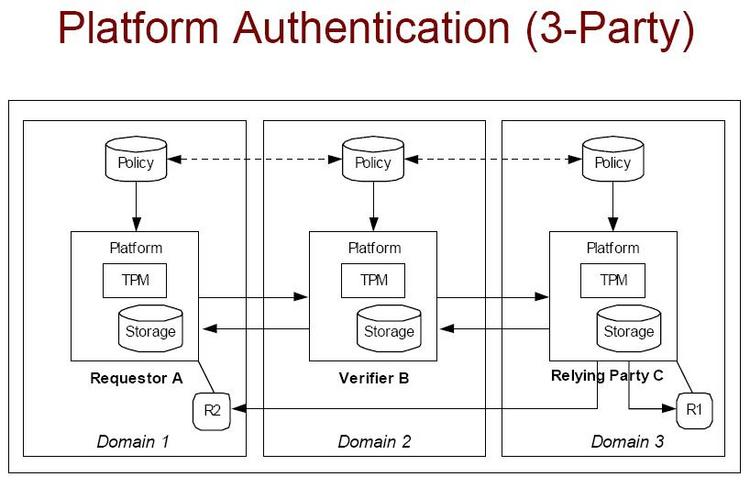
An emerging standard for Trusted Computing is a 'Trusted Platform', which will relay on a cryptographically secured module to hold identity information, certificates and secret keys that can be verified and exchanged in a trusted computing environment. These modules, or TPMs, are now available as is new software for identity management and attesting to the integrity of the underlying computing platform. There are also software versions of TPMs, some open source, that are able to play in a trusted environment, although they are less secure than hardware TP modules. See http://www.infsec.ethz.ch/people/psevinc/.
Here is a trusted computing network verification diagram:
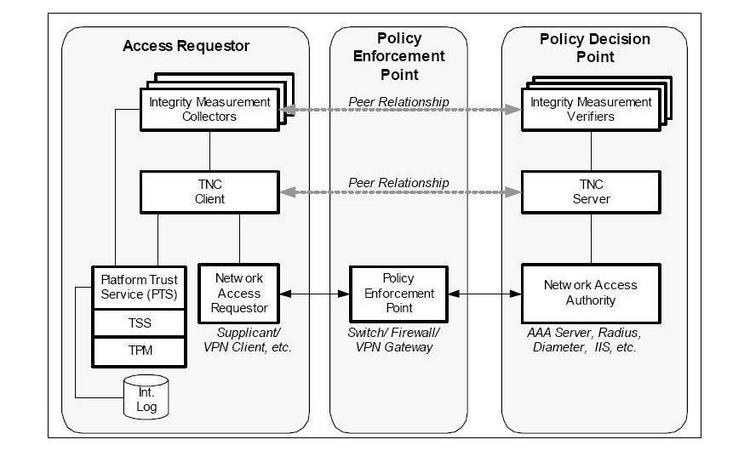
and, at a network level,Trusted Network Connection [TNC]:
Anti-spyware products are becoming almost as ubiquitous as anti-virus software. Almost all anti-virus, anti-worm vendors were adding or incorporating anti-spyware modules in their product lines. Symantec will be adding this as a feature to existing products while McAfee will be offering an anti-spyware additional module to its enterprise offerings.
Phishing was also a topic at many vendor presentations, even though this was largely referred as a social engineering attack. The Identity Management companies tried to link phishing with ID mgt, but generally required end-to-end use of their products. That long view of security gives birth to another TLA - UTM or "unified threat management" as Symantec CEO John Thomson called in his keynote.
Also there were renewed efforts to work together on an industry level.
A rare partnership between government and industry resulted in the Common Vulnerability Scoring System (CVSS), unveiled at the RSA Conference by the National Infrastructure Advisory Council [NIAC, a part of the U.S. Department of Homeland Security] and leading vendors like Cisco, Ebay, Microsoft, and Symantec. This new and ambitious system aims to provide a common descriptive language and standardized formula for reporting and assessing computer security vulnerabilities and issues, instead of varying and confusing vendor-specific ratings.
CVSS, which is partly related to Mitre Corp.'s CVE rating system, helps prioritize software vulnerabilities both for ISVs and for enterprise users, calculating the risk by considering the number of systems involved, the type of exploit required, and if a software patch is available.
Three major security and auditing groups announced the formation of a cooperative alliance to create better security policies and legislation and to better work with security professionals throughout the industry. These were the ASIS International, the ISACA (Information Systems Audit and Control Association) and ISSA (Information Systems Security Association). The groups will also work together to define certification and training requirements for the Chief Security Officer (CSO) role and other security-related positions in industry.
And Microsoft introduced its Microsoft Security Resource Center team at its booth where security issues could be addressed. This was mostly a customer feedback exercise and an attempt to raise the profile of the MSRC, which also ran a blog for the length of the conference. It ties into the TechNet security pages, [Finally, links for tools and patches.]
http://spaces.msn.com/members/msrc/PersonalSpace.aspx
http://www.microsoft.com/technet/archive/community/columns/security/essays/sectour.mspx
Underscoring the new Microsoft security initiatives, Bill Gates delivered the show's opening keynote address on Monday. It highlighted new Microsoft security products, including their enhanced 'Internet security and acceleration' [ISA] server and future identity management products, and touted a new version of Internet Explorer by this summer - but only for Win XP users.
Microsoft was a platinum sponsor and had about 100 employees at the show. Besides a large booth with a presentation area, there was a separate expo area where attendees could get 'hands-on' test experience with Microsoft security products and tools.
[After the RSA Conference, Gartner Corp analyst Neil MacDonald posted a critique of the latest MS security offerings, rejecting the incremental approach they are taking rather than a fundamental architectural change, particularly with its IE web browser. See:
http://www3.gartner.com/DisplayDocument?doc_cd=126360
Also in the critique: "The decision to restrict IE 7.0 to the XP platform also suggests that Microsoft wants to force users of older platforms to upgrade if they want improved security." ]
This and all other major keynotes are replayable [after RSA webcast registration] at:
http://2005.rsaconference.com/us/general/webcasts.aspx
Conference Tracks and Technical Sessions
Conference sessions were held in the afternoons in 16 simultaneous tracks, including two separate Hackers & Threats tracks, tracks for developers and cryptographers, business tracks, and tracks for privacy, web security, wireless and Identity & Access Management.
The Hacker Tracks definitely covered a lot of important ground and gave pause to developers and security officers alike. One paper focused on that old nemesis, SQL Injection, showing that it was still a major concern since the old standard approach of hiding error messages or using generic problem messages does not actually stop the hack.
The presentation, by Imperva's Ofer Maor, shows the result of security testing on MySQL and all leading DBs using indirect query tests to discover the number and type of data fields available to an SQL injection attack. These so-called 'blind' injection techniques only take a little more effort but still yield confidential data.
For instance, even with hidden or generic error messages an attacker could request additional fields above and below the actual number until the correct number was determined and also check the data type one field at a time until there was no error message or the target data emerged:
inject : ORDER BY 1 --
[and other numbers to get the right number of columns]
Assuming we get the number of columns, '4' here, and that we know a valid acctnum, (AccNum=11223344), we can use the following sequence with the the UNION SELECT clause to get the data types for the columns:
11223344) UNION SELECT NULL,NULL,NULL,NULL WHERE 1=2 --No Error - Syntax is right. MS SQL Server Used. Proceeding.11223344) UNION SELECT 1,NULL,NULL,NULL WHERE 1=2 --No Error - First column is an integer.11223344) UNION SELECT 1,2,NULL,NULL WHERE 1=2 --Error! - Second column is not an integer.11223344) UNION SELECT 1,'2',NULL,NULL WHERE 1=2 --No Error - Second column is a string.11223344) UNION SELECT 1,'2',3,NULL WHERE 1=2 --Error! - Third column is not an integer.11223344) UNION SELECT 1,'2','3',NULL WHERE 1=2 --No Error - Third column is a string.11223344) UNION SELECT 1,'2','3',4 WHERE 1=2 --Error! - Fourth column is not an integer.11223344) UNION SELECT 1,'2','3','4' WHERE 1=2 --No Error - Fourth column is a string.
From this point an attacker can craft more specific queries to
get system tables and eventually get, for example, CCnum, SSnum and other
sensitive variables.
This and other presentations are available only to full conference attendees but Imperva has several white papers on their website which were the basis for RSA presentation:
http://www.imperva.com/application_defense_center/glossary/sql_injection.html
http://www.imperva.com/application_defense_center/white_papers/blind_sql_server_injection.html
Maor also discussed how signature-based security tools could be thwarted by using other SQL tricks - concatenation, buried comments and use of character values for instance - to camouflage the injected SQL. Real security must be implemented at the application level and web masters and developers must be careful in their designs and coding and also very comprehensive in testing.
At the conclusion of the session, Maor suggested using different admin accounts and passwords for different tables and application functions as a deterrent. Also, while the occurrence of a certain SQL signature in a parameter value might not be enough to alert for SQL injection attack, the same signature in correlation with error responses or abnormal parameter size of other signatures may indicate an SQL injection attack.
Microsoft researchers Kurt Dillard and Mike Danseglio gave a Hacker track technical presentation on a new generation of stealthy rootkits for Windows kernels. These smarter root kits intercept system calls and actively filter out signs of their presence to avoid detection by software and security staff. Microsoft has posted a short white paper on file hiding and a 'cross-view diff' tool they are developing to detect this behavior:
http://research.microsoft.com/rootkit
Another presentation by Dan Houser on stopping script kiddies and automated attacks [for a mere $30K effort] suggested hiding critical servers in the open by using available IP addresses for virtual servers on an Internet-wide honey-pot. From the slides:
- Convert unused Class B and C IP address space into decoy tripwire nets
- example: 16,320,000 decoys, 200 "real" servers
- Stop swallowing packets: route unreachable hosts to the virtual honeynet
- 190,000 decoys per "real" server = 99.9995% detection
- Any hits are malicious - route to IDS / IPS
The result is that port scans would take weeks and even years to complete while source addresses for the attackers can be identified and blocked before real systems are compromised. This is approach also known as the Big Freakin' Haystack Initiative; see more at http://sourceforge.net/projects/bfhi.
Vendor News
Sun announced security enhancements to be added to its new Solaris10 OS, including an integrity checking process that provides assurance against accidental or malicious tampering. A future update to Solaris 10 will feature automatic run-time verification. This feature is designed to check the system's code at the exact moment of execution, protecting against the possibility of unauthorized modification between periodic auditing checks and actual use. Administrators will be able to customize which signatures will be checked, and use provided tools to digitally-sign code from other sources.
After 15 months of certification testing by an independent organization, Sun announced that its Solaris 9 Operating System has received 'Common Criteria Certification'. Common Criteria is a critical requirement to many governments, military and financial institutions. [Except for Sun's military-grade Trusted Solaris operating system, Solaris becomes the only general purpose operating system with protection profiles of both Controlled Access Protection Profile and Role Based Access Control at Evaluation Assurance Level 4+ (EAL4+). ]
Also, among Sun speakers at RSA conference this week was their Chief Security Officer, Whitfield Diffie, who headlined a cryptographers panel. Diffie is co-author of the Diffie-Hellman standard for Public Key exchange [PKI].
Hewlett-Packard's booth demonstrated an HP technology to limit the spread of viruses and worms throughout an enterprise by isolating problem PCs and workstations and limiting outbound bandwidth. Its new virus-throttling software will be available for ProLiant Servers and ProCurve Networking by HP 5300 series switches.
HP also announced its Security Containment suite for its HP-UX 11iv2 OS. This virtualizes application into domains and limits memory and file access by domains.
Other new products at RSA2005 used Linux, but it was often implicit rather than obvious:
Linux was 'inside' for many security appliances: many security appliances for email, VPNs, firewalls, etc., use embedded Linux at least as a guest OS for serial port terminal sessions. Some run their IDS on Linux. Some of the longer term appliance vendors use hardened freeBSD [Borderware, for example]. Sun uses ENEA's OSE [not Linux or secure Solaris], and a few use WindRiver's realtime OS, Vx Works. A few embedded Linux examples, most using a 2.6 kernel:
- Symantec appliances for firewalls, email, and network intrusion
- Foundry's web acceleration appliance
- ServGates EdgeForce line of all-in-one security appliances
- TippingPoint's UnityOne IPS and integrated security appliance, winner of SC Magazine's 2005 award for 'best security solution' and a true 1 Gps device, uses WindRiver Vx, but the companion SMS manager device uses Linux.
Novell introduced its Security Manager product, which is based on its SuSE Linux and runs on any standard PC server. The product includes firewall and VPN gateway, intrusion protection, virus protection, spam blocks and configurable content filtering. In this case, the underlying software comes from Astaro Networks which also sells it directly [about $300 for a server and a 10 device monitoring license].
Separation Anxiety
Conference security separated the different classes of attendees so successfully that it may become model of what other conferences will do. Not only were the badges and holders different for full-conference attendees, exhibitors, and expo attendees, the full-conference attendees had their photos on the badges.
Professional security company personnel were used instead of convention center part timers, so expo attendees were cleared out of the exhibition hall at certain times and only full conference attendees got to see Bill Gates keynote. Some vendors also provided expo perks to those with full-conference badges.
A theatrical presentation preceding the show's opening highlighted the prohibition and codebreaker theme. It told the story of honored codebreakers and security pioneers Elizabeth and William Friedman and how they helped start US government codebreaking hegemony in World War I and into the 1920s and 30s.
Opening ceremony awards were aimed at recognizing ongoing contributions to the advancement of information security. RSA 2005 recipients honored for these annual awards include: for public policy, Orson Swindle, Federal Trade Commission; for mathematics, Dan Boneh, associate professor, Stanford University; and for best security practices, Michael Assante, CIO at American Electric Power.
Collateral and Contests
There were more t-shirts, pens and other collateral offerings, indicating a healthier industry. Borderware, a provider of anti-spam and anti-virus software, offered a daily drawing for a 50-inch TV. There were also uncountable drawings for iPods and X-Boxes. Some vendors offered wheel-spins for PC and X-Box games [and mousepads for the not-so-lucky].
Three of the more useful collaterals were the CISSP [computer security professional certification] assessment CD from CA, the box set of Solaris10 DVDs from Sun [saves a really, really long series of downloads and at least 4 CD-Rs], and the numerous retractable Ethernet cables [like the older phone port connectors, only more useful.]
Special commendation in this department goes to McAfee who offered the current edition of "Hacking Exposed" - 737 pages - for only sitting through a short presentation and a short demo. Although they did finally run out of books, this was a great service toward promoting secure computing everywhere. I was very happy to get an updated copy!
And I was very happy to attend the 2005 RSA Conference and Expo.
If you are are interested and live nearby, RSA Conference will also be holding one-day regional events throughout the year including: September 13, 2005 in Chicago and September 15, 2005 in New York. For more information, visit http://www.rsaconference.com.
![[BIO]](../gx/authors/dyckoff.jpg) Howard Dyckoff is a long term IT professional with primary experience at
Fortune 100 and 200 firms. Before his IT career, he worked for Aviation
Week and Space Technology magazine and before that used to edit SkyCom, a
newsletter for astronomers and rocketeers. He hails from the Republic of
Brooklyn [and Polytechnic Institute] and now, after several trips to
Himalayan mountain tops, resides in the SF Bay Area with a large book
collection and several pet rocks.
Howard Dyckoff is a long term IT professional with primary experience at
Fortune 100 and 200 firms. Before his IT career, he worked for Aviation
Week and Space Technology magazine and before that used to edit SkyCom, a
newsletter for astronomers and rocketeers. He hails from the Republic of
Brooklyn [and Polytechnic Institute] and now, after several trips to
Himalayan mountain tops, resides in the SF Bay Area with a large book
collection and several pet rocks.

