Joey's Notes: Basic Samba Configuration
By Joey Prestia

Samba is a program that runs on Linux and allows seamless interaction between the Linux and Windows operating systems. By using Samba, your users can be using Windows and actually access their data on a Linux server. This benefits the administrator - in the form of ease of administration, along with the inherent security of Linux - while also benefitting the user through familiarity. This month's article covers basic setup of a Samba server for use as a user home directory server, and configuration for a simple group collaboration share.
"Microsoft's file access protocol [is] called the Common Internet File System (CIFS). CIFS is an interoperable mechanism for a client system to request file access from a server system in a network regardless of the underlying operating system platforms of the respective systems." [1] Samba has been adapted to use CIFS, which is actually an update to Server Message Block (SMB) protocol - which is what lies at the heart of SaMBa. It can even serve as a Primary Domain Controller (PDC). Some advantages are:
- Your users will never know that they are using a Linux server, so they won't have to learn a new operating system.
- You'll be able to centralize backups and administer a more secure environment.
- You'll be able to allow your users to use their Windows credentials to login and access their Linux home directories.
- You can share your Linux printers with your Windows clients.
The list goes on and on. More details can be found at http://us1.samba.org/samba/. Please keep in mind that Samba is a very rich, complex environment, and that what I am showing here just demonstrates its most basic operation.
I'll be using Red Hat Enterprise Linux 5.2 in this tutorial, with the
firewall disabled and SELinux set to "enforcing". Samba isn't installed by
default in RHEL 5, so, if you didn't select Windows File
Server packages at install time, you can install it by doing yum
(i.e., # yum install -y samba), or by using your distribution's
package manager. Ideally, having access to a Windows computer
located on the same network will allow you to see firsthand how Samba
works. (Note: If you want to allow Samba through your firewall, you
must allow access to ports 137-139.)
There are two daemons associated with Samba's basic operation: The first is smbd, which handles the Server Message Block protocol. The second daemon, nmbd, publishes WINS name service. WINS implements the NETBIOS nameserver protocol used by Windows systems. (This can be thought of as being a Windows-only version of DNS name mapping; somewhat confusingly, modern Windows systems support both WINS and DNS.) When connecting a Windows OS to a share, the syntax is \\NETBIOSname\sharename; this format is dubbed "Universal Naming Convention" (UNC). Samba's NMB daemon converts references to a machine's DNS hostname to its NETBIOS name if necessary; therefore, \\ipaddress\sharename will also work. There is a third daemon - Winbind, but it is for more-advanced configurations than I will be covering in this basic article.
First, assuming you have Samba and all its dependencies installed, we'll look at Samba's configuration file - /etc/samba/smb.conf. smb.conf has comments (indicated by #) and potential options (shown by semicolons). Both get ignored by Samba, and are present for readability purposes only.
Configuration of /etc/samba/smb.conf
Before we do anything else, let's back up this file (i.e., cp /etc/samba/smb.conf /etc/samba/smb.conf.orig), for safety. smb.conf is divided in two main sections, indicated by a line of equals signs '=' and either "Global Settings" or "Share Definitions" in the middle of them. Subsections are indicated by minus signs '-' with the name of the subsection in the middle of the line. Now, configuring /etc/samba/smb.conf for basic operation as a user's home directory server and a group collaborative share is really simple; in fact, it's almost ready out of the box. The first thing we will be concerned with is the Network Related Options subsection, under the Global Settings section. Look for the directive workgroup, and set this according to your needs. In this case, I will just set it to SAMBAGROUP. Later, I will have my Windows computer join the SAMBAGROUP workgroup. You can also change the server string; this may be especially desirable in a production environment, although I didn't do it for this tutorial. (By the way, it's always a really good idea when editing big configuration files like this to make a note, wherever you make a change. Additionally, leave the changed option's original value commented out rather than deleting it. This way, anyone working with the file later can see what was changed, who changed it, and why. You yourself at a later date may need this information when you need to troubleshoot or modify something.)
Common Global Options
Basic
| Directive | Expected Setting | Comment |
|---|---|---|
| workgroup | workgroup name | Maps to the Windows workgroup. |
| realm | kerberos realm | Specifies the Kerberos realm to use. |
| netbios name | netbios name | The NetBIOS name that the Sambe server is known by. |
| netbios aliases | netbios alias | Additional NetBIOS names that nmbd will map to the server. |
| server string | server description | This shows up in browse lists, next to the machine name. |
| interfaces | eth0 ip/netmask | Network interfaces to listen on. |
Security
| Directive | Expected Setting | Comment |
|---|---|---|
| security | user / share | If you have Linux users, then you want user; if using guest shares without passwords, then you would want share. |
| auth methods | guest / sam / winbind | Guest is anonymous, sam looks in local accounts, and winbind relays requests for remote users. |
| encrypt passwords | yes / no | Use encrypted passwords: this defaults to "yes". |
| client schannel | auto / yes / no | Controls client offering or requesting use of netlogon schannel. |
| server schannel | auto / yes / no | Controls server offering or requesting use of netlogon schannel. |
| passdb backend | smbpasswd / tdbsam / ldapsam | Specify which passwd backend to authenticate with. |
| guest account | nobody / ftp | Specify system account for guest user accesses and permissions. |
| invalid users | username / groupname | List of users to be denied login: '@' indicates a NIS group, '+' and group name searches the Linux group database. |
| valid users | username | List of users allowed login, if left empty then anyone can login. |
| admin users | username | Users to assume role of superuser. |
| read list | username | Users to be granted read-only access. |
| write list | username | Users to be granted write permissions. |
| printer admin | username | Users given printer administrative access. |
| hosts allow | IP, hostname, or IP/mask | Hosts to be granted access; may be tab-, space-, or comma-delimited lists. See hosts_access (5) man page for details. |
| hosts deny | IP, hostname, or IP/mask | hosts to be denied access; may be tab-, space-, or comma-delimited lists. See hosts_access (5) man page for details. |
Common Share Options
| Directive | Expected Setting | Comment |
|---|---|---|
| comment | text comment | A description of the share. |
| path | absolute Linux path | This is the Linux path - not the Windows path - to the share. |
| invalid users | username / groupname | List of users to be denied login: @ indicates a NIS group, '+' and group name searches the Linux group database. |
| valid users | username | List of users allowed login, if left empty then anyone can login. |
| admin users | username | Users to assume role of superuser. |
| read list | username | Users to be granted read-only access. |
| write list | username | Users to be granted write permissions. |
| read only | username | Users that cannot create or modify files; this will default to 'yes'. |
| guest ok | yes / no | If "yes", then no password is required and privileges of guest account apply (defaults to "no".) |
| guest only | yes / no | This allows only guest connections (default to 'no'.) |
| hosts allow | IP, hostname, or IP/mask | Hosts to be granted access; may be tab-, space-, or comma-delimited lists. See hosts_access (5) man page for details. |
| hosts deny | IP, hostname, or IP/mask | hosts to be denied access; may be tab-, space-, or comma-delimited lists. See hosts_access (5) man page for details. |
| browseable | yes / no | This setting governs whether the share is visible in the list of shares to browse (defaults to "yes".) |
Let's start with the Global Settings section, in the Network Related Options subsection. Again, both the pound (or hash) sign (#) and semi-colon (;) are acceptable comment markers.
# Edited on 7-2-08 by Joey changed workgroup and set NetBIOS name to server1 see below.
# workgroup = MYGROUP
workgroup = SAMBAGROUP
server string = Samba Server Version %v
; netbios name = MYSERVER
netbios name = SERVER1
Next, we'll set up a group collaboration share for our users, so let's go down to the "Share Definitions" heading. When scrolling through this file, notice that "homes" (users' home directories) are already enabled as shares, by default. Be careful; even though these directives look simple, always refer to the manpages for smb.conf(5) for explanation of anything you may be uncertain of.
Shares
I created my share at the end of the file, under Share Definitions. Once again, leave yourself a note for future reference. There's nothing worse than playing detective through a configuration file months and months later, trying to find out what was changed and why. Shares can consist of lots of options, but we will just stick to the basics here. I will give a brief explanation of the ones I use in this example. The first thing we see enclosed in brackets is the "sharename". This has no bearing on the Linux path. The Linux path can be anything appropriate; I would use a descriptive term and use the same term for the Linux path, so when you have several of them they are easy to keep straight. When setting up shares, you needs to keep in mind that a Linux path is not going to be the same as a Windows path. In Linux a share named [Winshare] with a path of path = /srv/samba/winshare would be referenced \\NETBIOSname\sharename in Windows, so, if our Linux machine were assigned a NETBIOS name of SERVER1 and the share were called winshare one way to connect to it from Windows would be to place \\SERVER1\winshare in the address bar and hit <ENTER>. At this point, you would get prompted for your credentials.
#============================ Share Definitions ==============================
[homes]
comment = Home Directories
browseable = no
writable = yes
[printers]
comment = All Printer
path = /var/spool/samba
browseable = no
guest ok = no
writable = no
printable = yes
# A publicly accessible directory, but read-only, except for people in
# the "staff" group
; [public]
; comment = Public Stuff
; path = /home/samba
; public = yes
; writable = yes
; printable = no
; write list = +staff
# Edited on 7-2-08 by Joey added winshare for test project group 'smbuser'
# don't forget about SELinux and permissions for this to work!
[Winshare]
comment = Samba test share
path = /srv/samba/winshare
hosts allow = 10.0.2.
browseable = yes
write list = +smbuser
Now notice how the IP address is set up on the "hosts allow" line: 10.0.2. allows access to all hosts on the 10.0.2. subnet. Below the "hosts allow" line is "browseable = yes"; this will allow users on the network to browse the network and see the share. Also note the "write list" - I gave group-wide write access to the smbuser group.
Testparm
The "testparm" command entered on the Linux command line parses the /etc/samba/smb.conf file, and checks it for syntax errors. When you have finished editing this file, run testparm and see if anything pops up. It will also output your configuration, so you can see the shares you have set up and whether things are set up correctly. You do not need SMB running to test the configuration.
[root@rhce-prep ~]# vi /etc/samba/smb.conf
[root@rhce-prep ~]# testparm
Load smb config files from /etc/samba/smb.conf
Processing section "[homes]"
Processing section "[printers]"
Processing section "[Winshare]"
Loaded services file OK.
Server role: ROLE_STANDALONE
Press Enter to see a dump of your service definitions
[global]
workgroup = SAMBAGROUP
server string = Samba Server Version %v
passdb backend = tdbsam
cups options = raw
[homes]
comment = Home Directories
read only = No
browseable = No
[printers]
comment = All Printers
path = /var/spool/samba
printable = Yes
browseable = No
[Winshare]
comment = Samba test share
path = /srv/samba/winshare
write list = +smbuser
hosts allow = 10.0.2.
[root@rhce-prep ~]#
Check that everything looks correct:
[root@rhce-prep ~]# mkdir -p /srv/samba/winshare [root@rhce-prep ~]# groupadd smbuser [root@rhce-prep ~]# useradd john -G smbuser [root@rhce-prep ~]# passwd john Changing password for user john. New UNIX password: Retype new UNIX password: passwd: all authentication tokens updated successfully. [root@rhce-prep ~]# chown .smbuser /srv/samba/winshare/ [root@rhce-prep ~]# chmod 2775 /srv/samba/winshare/
Allow for SELinux
As things stand, when SELinux is in enforcing mode, Samba just won't work with newly created directories; they don't have the correct SELinux context applied to them. To allow access and have SELinux still enforcing, we need to look to the comments in smb.conf. Under the SELINUX NOTES section (toward the top of the file), note that it tells you what most people miss: the SELinux boolean "samba_enable_home_dirs" must be set to on. The command is right there, in the comments. In addition to the home directories, we created a new directory that needs the SELinux context "samba_share_t" assigned to it. Again, smb.conf gives us the command we need to set the context for SELinux protection.
# If you want to share home directories via Samba, please run: # setsebool -P samba_enable_home_dirs on # # If you create a new directory you want to share, you should mark it as # "samba-share_t", so that SELinux will let you write into it. # Make sure not to do that on system directories, as they may already have # been marked with the SELinux labels. # # Use ls -ldZ /path, to see which context a directory has. # # Set labels only on directories you created! # To set a label, use the following: chcon -t samba_share_t /path
[root@rhce-prep ~]# setsebool -P samba_enable_home_dirs on [root@rhce-prep ~]# chcon -t samba_share_t /srv/samba/winshare/ [root@rhce-prep ~]# chkconfig smb on [root@rhce-prep ~]# service smb start Starting SMB services: [ OK ] Starting NMB services: [ OK ] [root@rhce-prep ~]#
Smbpasswd
In addition to configuring standard group access and permissions, Samba requires a different password-encoding algorithm, so we need to create Samba passwords for our users. For domain controller configurations, there are other advanced options for adding groups and users - but, for now, we will just stick with the basics. In addition, the user must exist on the system; you can't just create samba-only users. (Note that I created a regular user called "john", earlier.)
[root@rhce-prep ~]# smbpasswd -a john New SMB password: Retype new SMB password: [root@rhce-prep ~]#
Testing the setup with smbclient
The "smbclient" command allows connections to Samba server shares from the Linux command line. It will accept a username and password, as well as the location and name of the share to which you want to connect. The basic format of the command is shown below. You can use it in a variety of ways; I have included the one that I find easiest. Use -U to specify the username, which is immediately followed by the % separator and the password. Following that, on the same line, I have the Linux equivalent of a Samba location - double forward slashes, 'localhost', and a forward-slash separator, followed by the name of the share we are connecting to; the result of all this should be an smb:\> prompt.
smbclient -U user%password //localhost/share
[root@rhce-prep ~]# smbclient -U john%redhat //localhost/winshare
Domain=[RHCE-PREP] OS=[Unix] Server=[Samba 3.0.28-0.el5.8]
smb: \> ls
. D 0 Sun Aug 3 15:34:49 2008
.. D 0 Sun Aug 3 15:34:49 2008
63700 blocks of size 16384. 44363 blocks available
smb: \>
Testing it out on the Windows side
The true test is to get on a Windows box and see how all this looks from there. Test it out: Can you join the workgroup? Can you access your home directory? What about the share? The first thing I did was join my Windows computer to workgroup SAMBAGROUP, which of course required a reboot. I did this by going into Control Panel, System, and clicking on the "Computer Name" tab, then clicking on "Change" to rename the computer or join a domain, and selecting the Workgroup option to make this computer a member of the SAMBAGROUP workgroup. After rebooting, I opened My Computer and browsed to My Network Places, then to View Workgroup Computers.
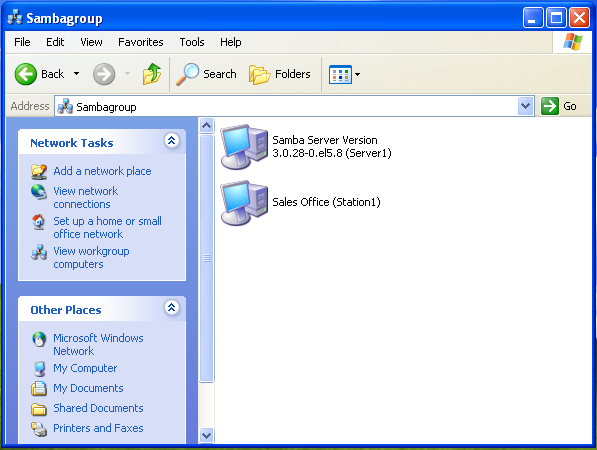
At this point, you can clearly see the words "Samba Server Version 3.0.28-0.el5.8" (the Samba server string). Depending on where you deploy your Samba server, you may not want to give anyone a starting point for hacking your setup; it only takes a second to hide the fact that you're running a Samba server from others that may have access to machines on your network. It is also important to consider whether you should make the shares visible on the network or not. I believe it's best to leave things on a need-to-know basis to prevent unnecessary problems. But, again, on things like this your company's policy should always be your guide. You should be aware that permissions - both in the smb.conf and on directories - are stacked; i.e., the most restrictive ones control what happens - so it is important to pay close attention to both.
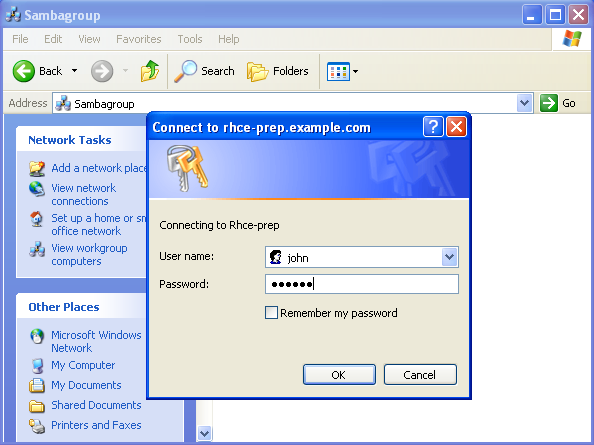
In this next image you can see where I clicked on Server1 and was presented with a login screen. If you're following along, you will have to present credentials at this point. We've also set up Samba for a group collaboration share and home directory server, and the options we selected in our share definitions dictate what will occur at this point.
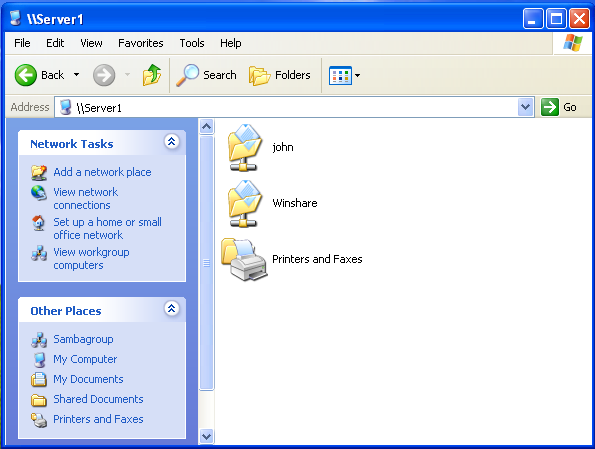
In the following image, we are able to view available printers that are available by default. We can also see user john's home directory, along with our newly created Windows share 'Winshare'.
Briefly, this is basic configuration of a Samba server for use as a Windows home directory server and simple group collaboration share server. Samba works out of the box with little or no configuration for a lot of purposes, and can be configured to act as a Primary Domain Controller for a network. This is a significantly more complex task, and requires a great deal of time spent learning the various options and security measures and implementing them correctly. It is easy to assume, because something can be so easy to set up, that it is overly simplistic and therefore implement it in a haphazard way.
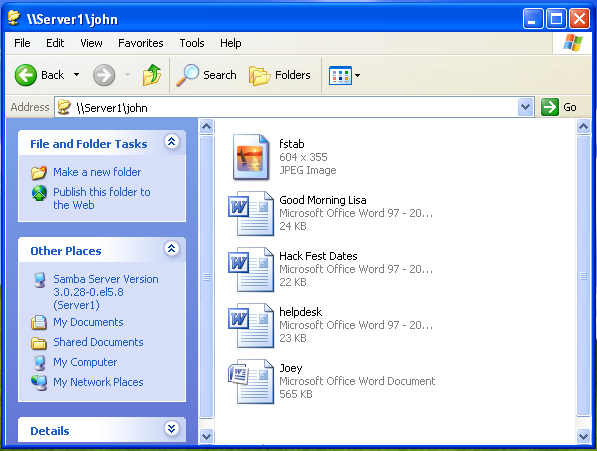
In this last figure, we will access user "john's" home directory. As you can see, he can work from Windows without problems, not even realizing he was in reality working on a Linux server.
Samba Web Administration Tool
The Samba Web Administration Tool (SWAT) tool allows an administrator to configure Samba via Web interface. It is an excellent way for new Samba administrators to get additional information on options available when setting up Samba. It is also commonly used by seasoned Samba administrators, because of its ease of use and advanced displays. It allows the administrator to start and stop daemons, see advanced possible configurable options, look up definitions for those options, and get help. It comes with some downsides: it is insecure and therefore not a good idea to use remotely. Additionally, using it overwrites smb.conf, which contains valuable comments.
Resources
[1] Document containing details of Microsoft's Common Internet File System (CIFS) File Access ProtocolTalkback: Discuss this article with The Answer Gang
![[BIO]](../gx/authors/prestia.jpg)
Joey was born in Phoenix and started programming at the age fourteen on a Timex Sinclair 1000. He was driven by hopes he might be able to do something with this early model computer. He soon became proficient in the BASIC and Assembly programming languages. Joey became a programmer in 1990 and added COBOL, Fortran, and Pascal to his repertoire of programming languages. Since then has become obsessed with just about every aspect of computer science. He became enlightened and discovered RedHat Linux in 2002 when someone gave him RedHat version six. This started off a new passion centered around Linux. Currently Joey is completing his degree in Linux Networking and working on campus for the college's RedHat Academy in Arizona. He is also on the staff of the Linux Gazette as the Mirror Coordinator.

